
According to a 2014 Gallup poll, having a credit card stolen by computer hackers is an American’s greatest fear – a figure that is no surprise considering that cybercrimes are on the rise.
What might surprise you is that for some businesses, hacking isn’t always seen as a threat. In fact, companies like Apple are paying hackers to expose vulnerabilities and flaws in their products.
These tech-savvy, code-breaking do-gooders are known as “ethical hackers” – and with data breaches costing an average of $158 per record lost or stolen, the demand for their services is growing.
We were curious about these honorable computer spies, so we asked 50 ethical hackers to tell us about who they are, what they do, and, most importantly, what they know about the potentially severe hacks of the future. Keep reading to see what they told us.
MEET THE ETHICAL HACKERS
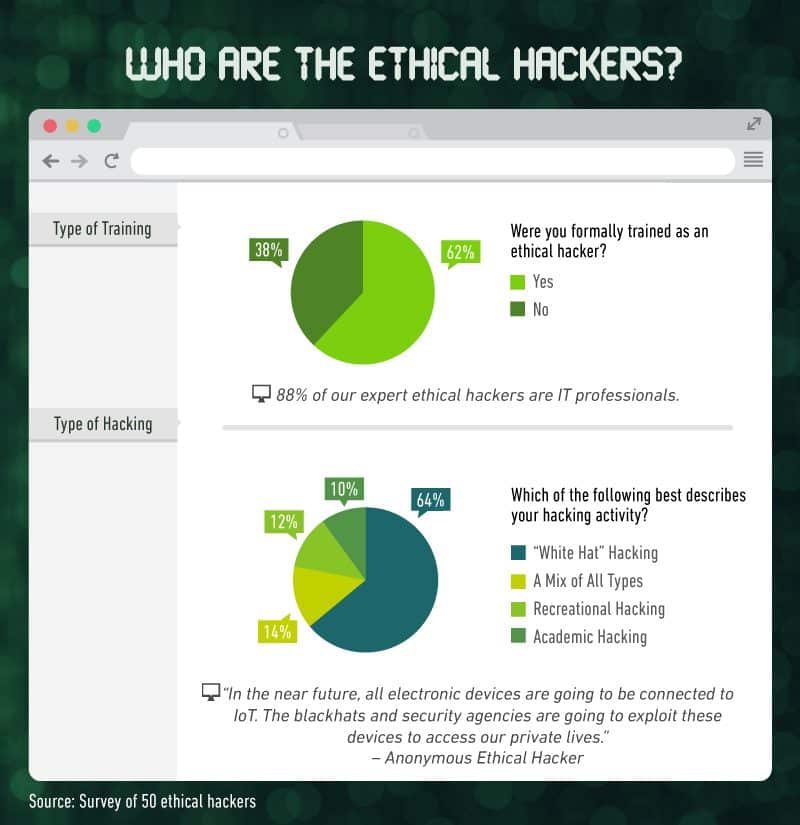
First, we asked the hackers about themselves. How did they learn how to break through computer securities, find system backdoors and code viruses, and discover vulnerabilities even missed by big shots at tech firms?
As it turns out, 88 percent of the ethical hackers surveyed are IT professionals and have spent their careers working with computers, systems, and programs. Sixty-two percent are self-taught, which makes sense considering that two-thirds of professional developers are also self-taught and fewer than half hold a formal computer science degree.
Additionally, 64 percent consider themselves to be white hat hackers – specialists who break into protected systems and networks to test their security.
CATASTROPHIC HACKS OF THE FUTURE
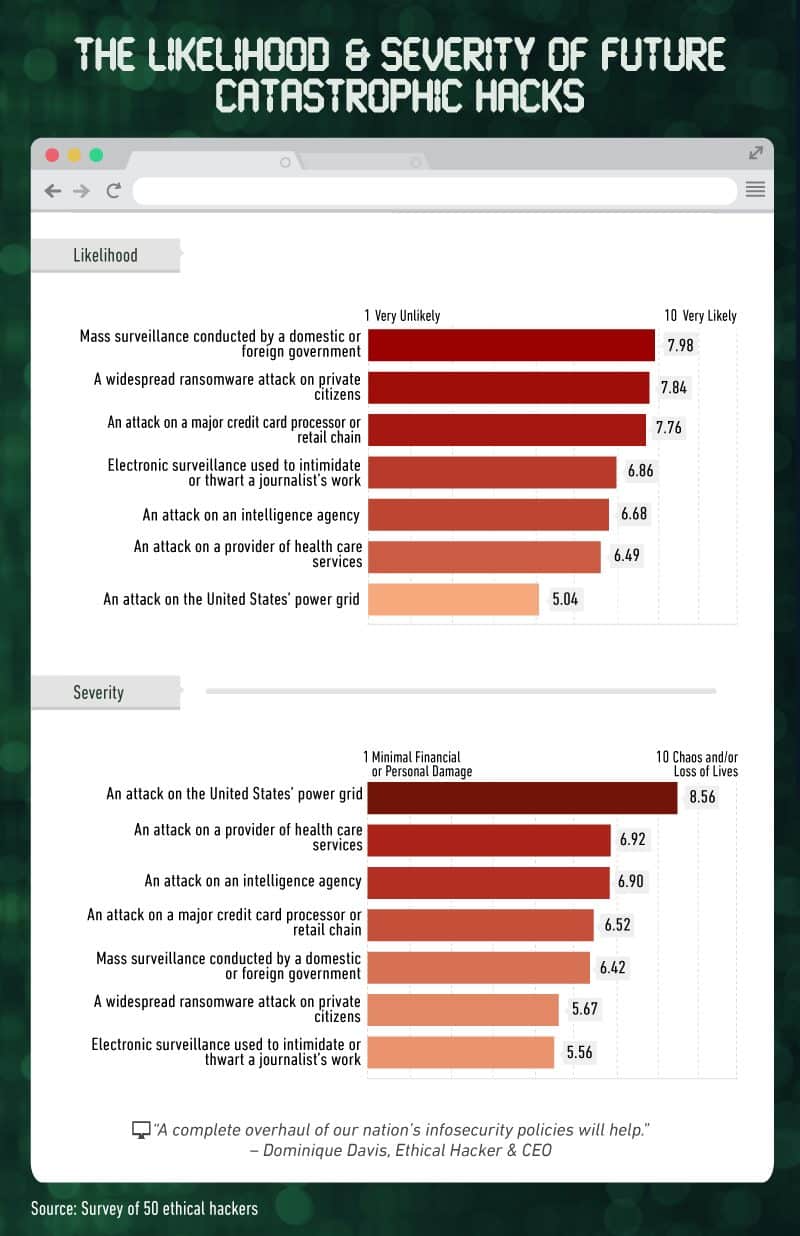
Next, we asked our ethical hackers to assess the risk of future catastrophic hacks. How likely is it that the government (ours or someone else’s) will surveil us en masse, that a hacker will break into and attack an intelligence agency, or that a major credit card processor will fall victim to hacking?
Hackers ranked high danger across the board. Out of a scale of 1 (very unlikely) to 10 (very likely), the possibility of a mass surveillance conducted by a domestic or foreign government was given a rating of 7.98 by our survey respondents. But mass surveillance isn’t just something we need to worry about in the future. Edward Snowden was a whistleblower who leaked top-secret documents in 2013 about NSA surveillance activities, and there’s evidence this type of activity continues today.
A widespread ransomware attack on private citizens (7.84) and an attack on a major credit card processor or retail chain (7.76) are just as likely, according to our ethical hackers. But how much would these attacks impact our lives?
The attack that was ranked as having the highest severity was an attack on the U.S power grid (8.56); however, it was ranked the least likely to actually take place (5.04). Our hackers were also concerned about breaches against health care providers, intelligence agencies, and credit card processors.
WHO ARE THE VILLAINS?
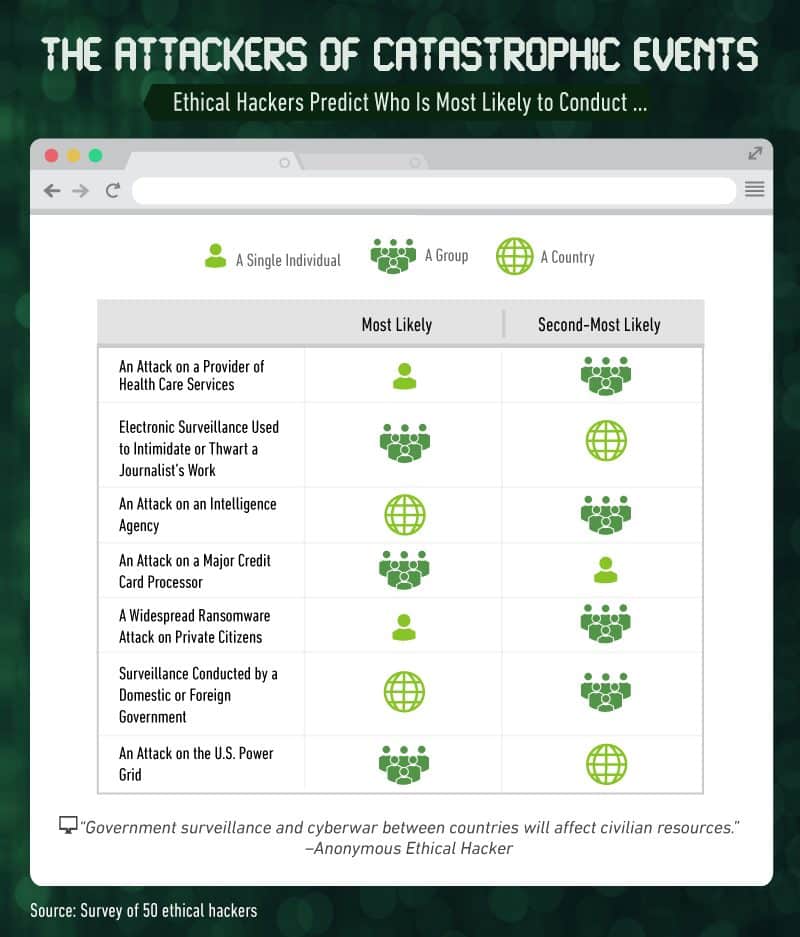
If our ethical hackers are considered anti-heroes who help technology companies, then black hat hackers are our villains; they’ll identify those same vulnerabilities, but they’ll also exploit them.
According to our experts, health care is most vulnerable to attacks by single hackers, however, groups are also a threat. Intelligence agencies are a target for foreign countries, but journalists, our hackers say, are most likely to be attacked by a group of hackers. Still, modern journalists may disagree and call our own government the greatest threat.
ARE YOU VULNERABLE?

The large majority of our ethical hackers agree that no security program available is completely effective at preventing cyberattacks. As much as we wish otherwise, technology is vulnerable.
Of course, that’s no reason not to try to defend ourselves. While only 10 percent of our ethical hackers agreed Bitdefender was the most effective security or virus protection program, it still received higher marks than any other program.
If you want to make your own technology safer, hackers recommend staying away from Windows,which makes sense since it is the most popular operating system (and thus more targeted). Furthermore,Windows wasn’t built for security (while Mac and Linux systems were).
Our hackers also ranked device vulnerability and said that routers were the most easily accessible, followed by desktops, laptops, and mobile devices.
HOW HACKER TRAINING IMPACTS PREDICTIONS
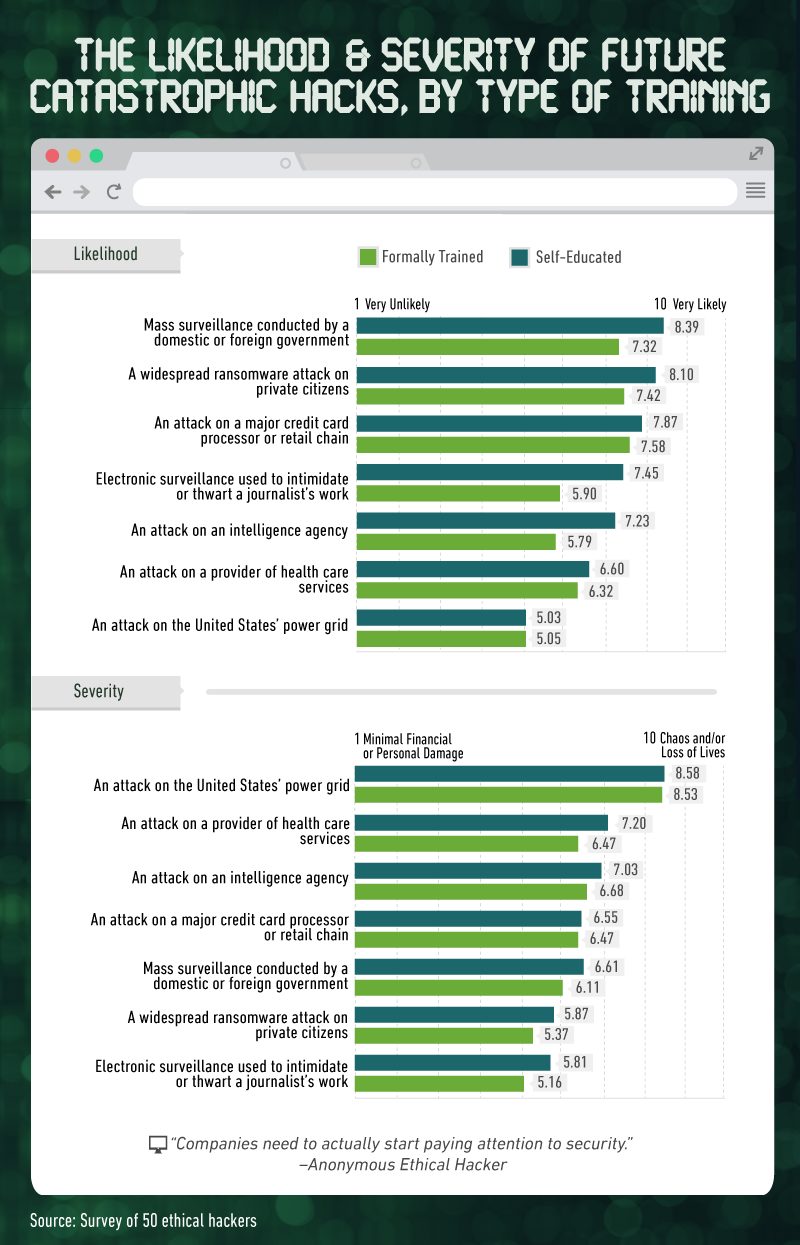
While all our ethical hackers pretty much all agreed that we’re vulnerable, some were more concerned than others. And that concern correlated with training. Self-taught hackers (the majority of those surveyed) displayed more concern across the board about catastrophic hacks.
The only case in which this attitude changed was when we asked about an attack on the power grid.Formally trained hackers displayed slightly more concern about the power grid than self-trained hackers.

The only attacks they disagree on? Health care – which formally trained hackers pin on a single individual, while self-taught hackers believe it’s most vulnerable to a group. And journalist surveillance? Formally trained hackers believe both a single individual and a group are equally likely to carry out a hack, while self-taught hackers are betting on a group alone.
It’s hard to say why the groups disagree on only two threats, but as for health care, both are right. A recent hack by an individual compromised 655,000 health care records, and a groupheld an entire hospital hostage using ransomware.
KEEPING OUR DATA SAFE
Ethical hackers agree: There’s no way to keep our data 100 percent safe. But some devices, technologies, and companies are more vulnerable than others. So how do we put that information to use? Start by choosing a less vulnerable technology (like a Mac or Linux system instead of a Windows PC), and dedicate time and resources to security in your own business (if you own one). Finally, make sure you have hard-to-crack passwords and security questions as an individual.
METHODOLOGY
We surveyed 50 ethical hackers by contacting them through Upwork and LinkedIn. Ethical hackers were found on LinkedIn using Umbra Security’s List, and respondents from this list included Dominique Davis and Tony Zafiropoulos. Upwork respondents had “Ethical Hacker” listed on their profile. Respondents were only quoted if they gave permission.
SOURCES
- http://www.gallup.com/poll/178856/hacking-tops-list-crimes-americans-worry.aspx
- https://www.theguardian.com/small-business-network/2016/feb/08/huge-rise-hack-attacks-cyber-criminals-target-small-businesses
- http://www.cnbc.com/2016/08/05/apple-is-offering-up-to-200000-for-hackers-to-find-flaws-in-its-products.html
- http://www.itproportal.com/2015/11/26/the-growing-demand-for-ethical-hackers/
- http://qz.com/649409/two-out-of-three-developers-are-self-taught-and-other-trends-from-a-survey-of-56033-developers/
- http://www.biography.com/people/edward-snowden-21262897
- http://www.computerworld.com/article/3090566/healthcare-it/hackers-are-coming-for-your-healthcare-records-heres-why.html
- http://www.ibtimes.com/hackers-ransom-attack-california-hospital-more-proof-healthcare-cybersecurity-2309720
- http://www.zdnet.com/article/the-federal-government-on-what-are-the-most-popular-us-end-user-operating-systems/
- http://www.howtogeek.com/141944/htg-explains-why-windows-has-the-most-viruses/
- http://www.ibtimes.com/hollywood-hospital-held-hostage-hackers-asking-36m-ransom-release-network-malware-2308094?utm_source=internal&utm_campaign=incontent&utm_medium=related1
- http://www.journalism.org/interactives/investigative-journalists-on-surveillance/
- http://www.computerworld.com/article/3088907/security/hacker-selling-655-000-patient-records-from-3-hacked-healthcare-organizations.html
- http://thenextweb.com/insider/2014/09/03/protect-hackers-least-make-difficult/#gref

