The global pandemic of 2020 has not only changed the way we live and work now, it has altered the course of our lives moving forward. For better or worse, there are things that have changed during the pandemic that will never go back to the “normal” we knew before the coronavirus struck.
Some of these changes moving forward are for the better. Telemedicine is nowhere to stay making the healthcare system more efficient and convenient for doctors and patients. People will also be able to work from home more in the future saving time and money on commutes and allowing for a better work/life balance.
Unfortunately, some of these changes are bad for society. One thing that has increased during COVID and is here to stay is ransomware attacks. According to the FBI, during the height of the pandemic, ransomware attacks increased by 300% – 400%. Internationally, INTERPOL reported a 569% increase in malicious domain registrations from February to March 2020 and a 788% increase in high-risk registrations during that period.
Ransomware attacks are increasing and, in the coming year, will continue to be one of the biggest forms of cybercrime around. MonsterCloud, a leading expert in cyberterrorism and ransomware recovery, has analyzed the stats, surveys, and studies to find the ransomware trends that will loom large in 2021 and beyond. Here are the MonsterCloud reviews of the top ransomware threats for 2021.
Ransomware as a Service
As with a lot of technology, ransomware is becoming easier to find and implement for criminal organizations around the world. Hackers no longer have to develop their own ransomware programs to deploy, there are now ransomware gangs that have ransomware software ready to sell as a service to anyone who is interested.
Just like Software as a Service (SaaS) products, Ransomware as a Service (RaaS) gives relatively cheap and easy access to these types of malicious programs for a much smaller fee than the cost of creating it on your own. RaaS providers generally take a 20% – 30% cut of the ransom profit generated.
There are dozens of both established and new and emerging RaaS gangs in 2020. In 2021, there are a few who are rising to the top of the “industry”. These gangs have already provided ransomware for attacks that have cost businesses millions of dollars. The ransomware gangs which will continue to dominate the headlines in 2021 Include:
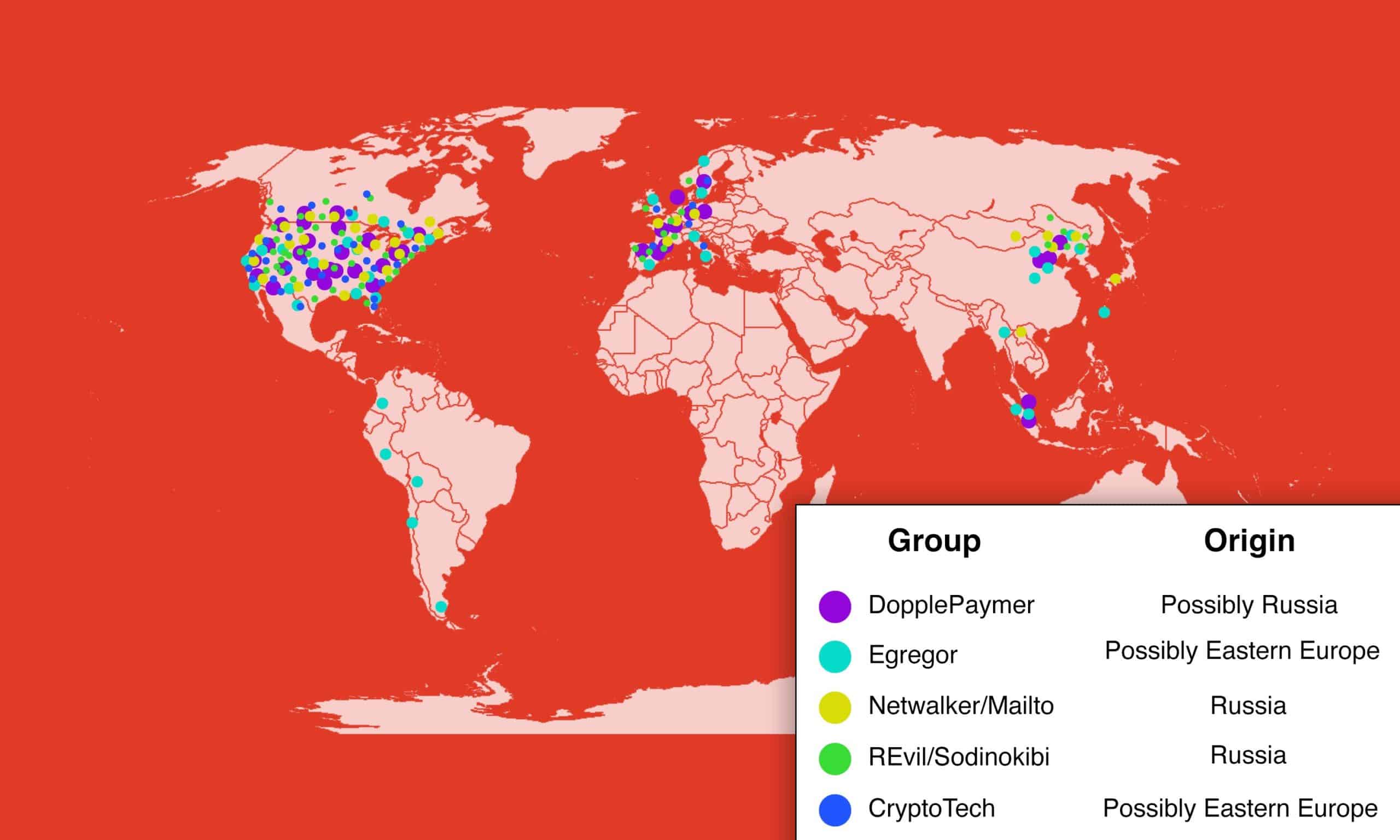
- DopplePaymer – provided ransomware for attacks on Pemex in Mexico, Bretagne Télécom in France, and both Newcastle and Düsseldorf University.
- Egregor – provided ransomware for attacks on Crytek in Germany, Ubisoft in France, and Barnes & Noble in the U.S.
- Netwalker/Mailto – provided ransomware for attacks on Toll Group in Australia as well as Equinix, UCSF, and Michigan State University in the U.S.
- REvil/Sodinokibi – provided ransomware for attacks on Britain’s Travelex, as well as airports and local governments in the U.S.
- Ryuk – the biggest RaaS gang was responsible for almost 33% of all attacks in 2019, including Sopra Steria in Europe and Seyfarth Shaw Law Firm, Universal Health Systems, and several other individual hospitals in the U.S.
Healthcare-related Attacks Will Continue
The global COVID-19 health crisis has led to healthcare systems around the world being stressed and spread thin. This leaves these types of organizations very vulnerable to ransomware. It also means they are more likely to pay ransoms instead of investing time in recovering data.
In 2020, there has already been a large uptick in cyberattacks on the healthcare system. The Associated Press reports that 59 U.S. health care providers or systems have been targeted by ransomware attacks. These attacks have affected patient care at 510 facilities around the country.
In Q3 of 2020 alone, there was a 50% increase in daily ransomware attacks from the previous two quarters. Attacks on the healthcare industry around the world have doubled in this last quarter as have the total number of attacks on the U.S. The other countries that have seen the biggest growth in ransomware attacks in Q3 include, India, Sri Lanka, Russia, and Turkey, respectively.
This trend already looks like it will only get worse. In October 2020, several departments of the U.S. Federal government including the Health and Human Services Department, the Cybersecurity and Infrastructure Security Agency, and the FBI issued a warning about immanent ransomware attacks on the healthcare industry. The announcement specifically mentions Ryuk as a potential attacker.
Increase in Mobile Ransomware
Many businesses are getting savvier about protecting their computers and networks from ransomware by using companies like MonsterCloud to put an IT plan in place to stop threats before they happen. Cybercriminals are not deterred though. They are using this as an opportunity to move to a different medium, mobile attacks.
According to Kaspersky, a leading antivirus software company, mobile ransomware attacks have been continually increasing over the last year. The numbers by quarter in the last year have increased every period from Q2 of 2019 to Q2 of 2020. The total amount of worldwide reported mobile ransomware attacks look like this:
- Q2 2019 – 753,550
- Q3 2019 – 870,617
- Q 4 2019 – 980,993
- Q1 2020 – 1,152,662
- Q2 2020 – 1,245,894
The top 5 ways ransomware gangs are attacking mobile devices are:
Conclusion
There are plenty of reasons why 2020 has been a very bad year. The incredible increase we have seen in ransomware this year is simply another problem this year has brought on. In 2021, many of the ransomware trends we have seen in 2020 will, unfortunately, continue and maybe even grow worse.
In the coming year, we will continue to see Ransomware as a Service gangs gain clients and provide software for more attacks. We will see our vulnerable healthcare system continue to take on an increased amount of attacks. And, our mobile phones will become a bigger target than ever.
If you are worried about these 2021 ransomware trends or any others, don’t worry, MonsterCloud can help. In addition to being a leader in ransomware removal, they can also help you protect your business before an attack happens, put plans in place to mitigate the damage if an attack comes and recover fast after an attack.
MonsterCloud reviews your cybersecurity to make sure you are protected from an attack happening, or happening again. They have successfully worked with over 1,000 victims of ransomware attacks. They have also successfully removed and recovered the affected data within 24 to 48 hours in 97.4% of cases.
About MonsterCloud
MonsterCloud is a leading authority on cyberterrorism and ransomware and is home to some of the world’s most renowned ransomware removal experts. Founder and CEO Zohar Pinhasi is a Counter Cyberterrorism Expert, Cyber intelligence threat specialist, and Ransomware Recovery Expert with nearly 25 years of experience in cybersecurity.
The company is a leader in ransomware removal and managed cybersecurity services and is backed by former FBI Deputy Director John Pistole. MonsterCloud has provided cyber threat intelligence to some of the world’s top authorities, including The Federal Bureau of Investigation (FBI) and dozens of police departments and municipalities across the United States and is a member of “No More Ransom” organization, an initiative by the Europol’s European Cybercrime Centre, among others, whose goal is to thwart ransomware.
Sources
https://securelist.com/it-threat-evolution-q2-2020-mobile-statistics/98337/
Fair Use Statement
You may share this content (for noncommercial purposes) to the clouds and back – just link the materials to this page. And while you’re at it, please credit us too!

